Digitalization and IoT provides numerous advantages for building owners and operators and their product and service providers. Modern digital platforms and products show greater usability and flexibility, higher asset and energy efficiency, and reach new levels of user comfort. Furthermore, modern digital platforms are open and extensible to fit evolving market requirements, but digitalization also presents security challenges.
Cyber attacks are a constant and increasing threat due to the ubiquitous connectivity that makes digitalization possible. In today’s connected world, the likelihood of a cyber attack is high. How do you confidently address such cyber threats? By taking a holistic approach to security measures across all aspects of your organization, building assets and automation systems. This includes making sure the building automation systems that manage your facility’s infrastructure are secure.
At J2 Innovations, we have taken the next step in providing best in class cyber security with the release of the latest FIN Framework, FIN 5. We’ve adopted a “think security” philosophy in the development and advancement of our FIN Framework product. This paper provides insight into how J2 Innovations has approached cyber security with the release of FIN 5, and continues to do so along the entire lifecycle.
Before diving in, let’s first discuss what cyber security means. We define cyber security as the protection of life and company assets from harm caused by digital attacks against the availability, confidentiality, integrity, authenticity, and reliability of information in cyberspace. Cyberspace is the complex system of interaction between people, software, and services that is facilitated by using technical means to connect them to the Intranet and Internet.
Let’s also define what it means to take a holistic approach to security. There are four key factors that impact security strength: people, communication, processes, and technology.
In general:
The spectrum of security challenges is broad. While physical threats are more obvious and change less often, cyber challenges can be more nefarious due to an everchanging threat landscape. When it comes to aligning security with business needs and the inevitable move toward convenience, we put a focus on cyber security from the outset.
Cyber attacks are among the fastest growing criminal activities today. They range from insider threats, ransomware attacks, opportunist threats, and hacktivism, all the way up to business espionage, terrorism, and state-sponsored cyber terrorism. Keeping organizations like yours safe and operating as usual takes a holistic approach to security.
J2 Innovations is committed to evolving FIN Framework so users can respond to a fast, complex, and constantly changing threat landscape. Our commitment is multifaceted. Our end-to-end approach to product development builds in security from the beginning. We call it "Security by Design". It includes an ongoing cycle of testing, enhancements, and evolution to keep our products and solutions at the forefront. In addition, we are part of Siemens, and jointly participate at the Charter of Trust, a global effort to develop and implement rules for ensuring cyber security throughout the networked environment. Simply put, we design with security in mind. We also contribute to and follow leading international standards such as ISO/IEC 62443 and OWASP as cyber security guidelines.
The effectiveness of a product’s cyber security design is attributed to the expertise of the development team. As part of our "Security by Design" methodology, we invest not only in technology developments for digital protection and product security, but also in the training required to maintain high levels of employee cyber security expertise.
Throughout the lifecycle of the product, our experts perform security threat and risk assessments (called TRAs) to address expected risk in the intended application of use. This assessment starts at the beginning of the process and is repeated as required to identify and mitigate risks appropriately.
In addition, regular product security testing is conducted by Siemens AG and external experts who use both manual penetration tests and automated machine security testing. The idea is to break the system in order to secure it. This testing ensures that the FIN Framework meets our security requirements. The test results are recorded and used to identify any necessary corrective actions.
FIN Framework is an open and robust platform for smart buildings, smart equipment and IoT that is at the center of creating efficient, sustainable and comfortable environments. It is also highly extensible so that OEM partners can customize the product to meet their specific market and customer requirements. As a software platform that functions as the heart and brain of a building, security by design is an essential pillar.
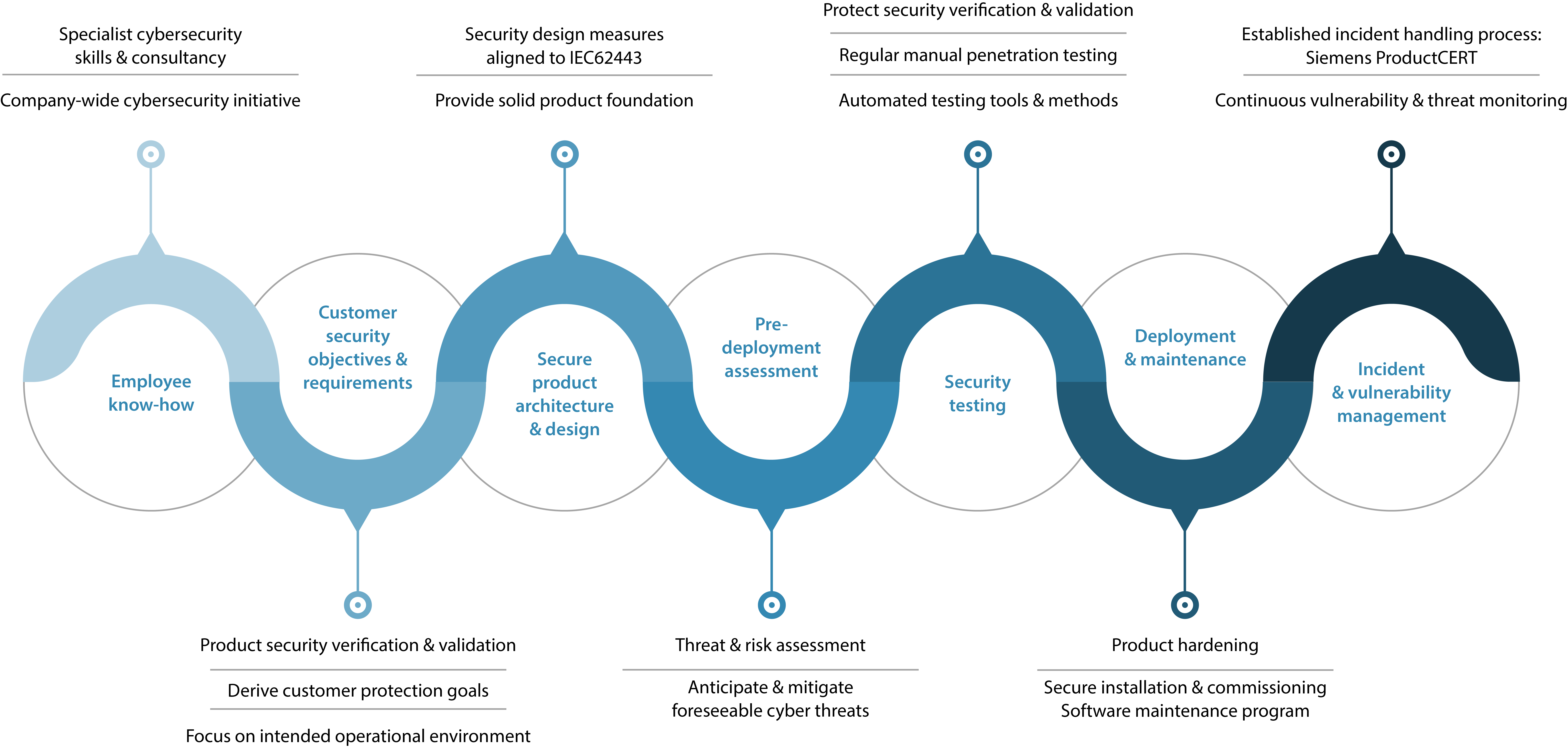
Our FIN Framework design experts adhere to the Siemens company-wide cyber security initiative as illustrated in the figure above. They follow the mandatory internal security policy that provides measures for ongoing development of FIN Framework products in accordance with the appropriate security level. FIN Framework products are aligned with ISO/IEC62443.
These measures help ensure that coding leads to secure product architecture, as well as secure implementation of software components. The software is designed to be secure by default when installed, which means certain features and functions are secure out-of-the-box. As new security threats continue to unfold, we continuously enhance and evolve the FIN Framework. We’ve integrated the following elements to make the FIN Framework secure by design:
As part of our life-cycle management (LCM) for FIN Framework, we periodically release patches, updates, and platform upgrades that remove new known vulnerabilities and protect FIN Framework against threats. Patches and updates are made available as they are developed, supported by access to a technical hotline run by product experts. By participating in LCM (which is free of charge in the 1st year after license purchase), you not only gain access to latest innovation and new functionality, but also to latest improvements in product robustness and cyber security.
We publish cyber security hardening guidelines to support the secure commissioning and deployment of FIN Framework products. These guidelines describe how the system needs to be configured in-order to ensure secure operation of the FIN Framework product in the intended operating environment. Configuration guidance includes: applications to install, which settings to activate or deactivate, firewall configurations, and the setting of user and system accounts and access rights. The hardening guidelines are maintained throughout the product lifecycle.

If a security issue or vulnerability is detected in a FIN Framework product or solution, we have incident and
vulnerability handling processes in place.
Incident and Vulnerability Handling Process: Our support mechanism for customer-reported security issues is illustrated in Figure 3. Vulnerabilities and/or incidents are submitted to our technical support team, which is supported by the global Siemens ProductCERT team that operates on a 24/7 basis. The necessary steps are taken to handle the situation and the incidents and remedies are disclosed.
Vulnerability Management: This is our internal detection process for fine-tuning the security of our products and solutions. Continuous threat monitoring allows us to detect and fix potential vulnerabilities in our products. FIN Framework software components are registered so that if any security vulnerabilities are found, the necessary remedies can be implemented and disclosed. Identified vulnerabilities are announced by the ProductCERT team via the ProductCERT security advisories.
As the leading open platform for smart buildings, smart equipment and IoT, J2 Innovations understand the challenges faced in meeting cyber security needs in today’s world. Our comprehensive security approach to the product lifecycle means our FIN Framework is designed with your security in mind. This ensures that FIN Framework can be part of a holistic approach to security that takes people, processes, technology, and communication into account.
Ultimately, smart organizations make security one of the cornerstones of their businesses today. FIN Framework is a flexible and interoperable portfolio that can be scaled to meet the needs of your organization. FIN Framework is Security by Design.
