Secure by Design
Peace of mind through cybersecurity
As the leading open platform for smart buildings, smart equipment and IoT, we understand the challenges you face in meeting your cybersecurity needs in today’s world. Our comprehensive security approach to the product lifecycle means our FIN Framework is designed with your security in mind.
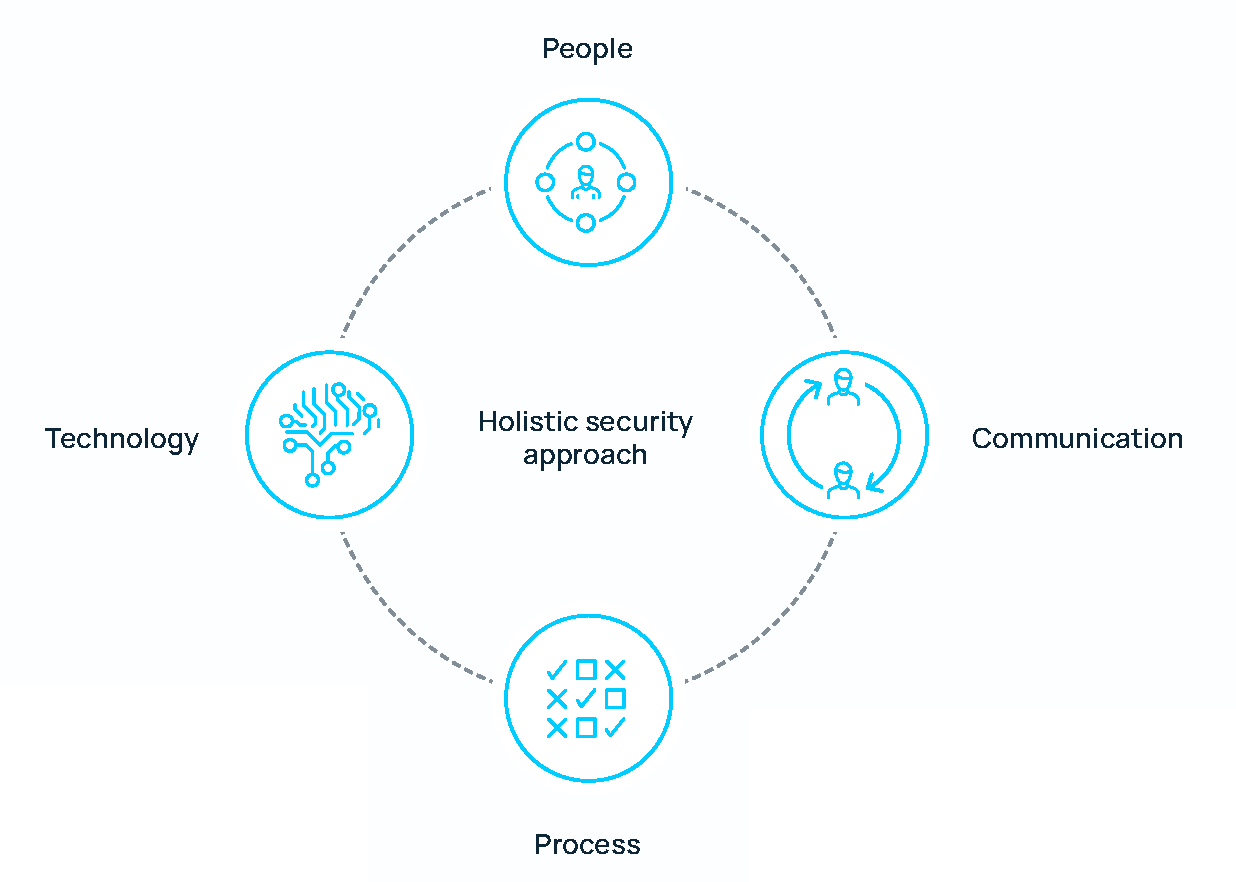
This ensures that FIN Framework can be part of your holistic approach to security that takes people, processes, technology, and communication into account. Ultimately, smart organizations make security one of the cornerstones of their businesses today. FIN Framework is a flexible and interoperable portfolio that can be scaled to meet the needs of your organization. FIN Framework is Security by Design.
FIN Framework
At J2 Innovations, we have taken the next step in providing best-in-class cybersecurity with the release of the latest FIN Framework.
We’ve adopted and continue a “think security” philosophy in developing and advancing our FIN Framework product.
Cyberspace is a complex system of interaction between people, software, and services that are facilitated by using technical means to connect them to the Intranet and Internet. By taking a holistic approach to security, we focus on four key factors that impact security strength: people, communication, processes, and technology.
The spectrum of security challenges is broad. While physical threats are more obvious and change less often, cyber challenges can be more nefarious due to an ever-changing threat landscape. When it comes to aligning security with business needs and the inevitable move toward convenience, we put a focus on cybersecurity from the outset.
Security by Design
Holistic Approach
Keeping organizations like yours safe and operating as usual takes a holistic approach to security.
Evolving
J2 Innovations is committed to evolving the FIN Framework so users can respond to a fast, complex, and constantly changing threat landscape.
Multifaceted
Our end-to-end approach to product development builds in security from the beginning. We call it Security by Design. It includes an ongoing cycle of testing, enhancements, and evolution to keep our products and solutions at the forefront.
Charter of Trust
We are part of the Siemens group and jointly participate in the Charter of Trust, a global effort to develop and implement rules for ensuring cybersecurity throughout the networked environment.
Security in mind
We design with security in mind. We contribute to and follow leading international standards such as ISO/IEC 62443 and OWASP as cybersecurity guidelines.
Security by Design Expertise
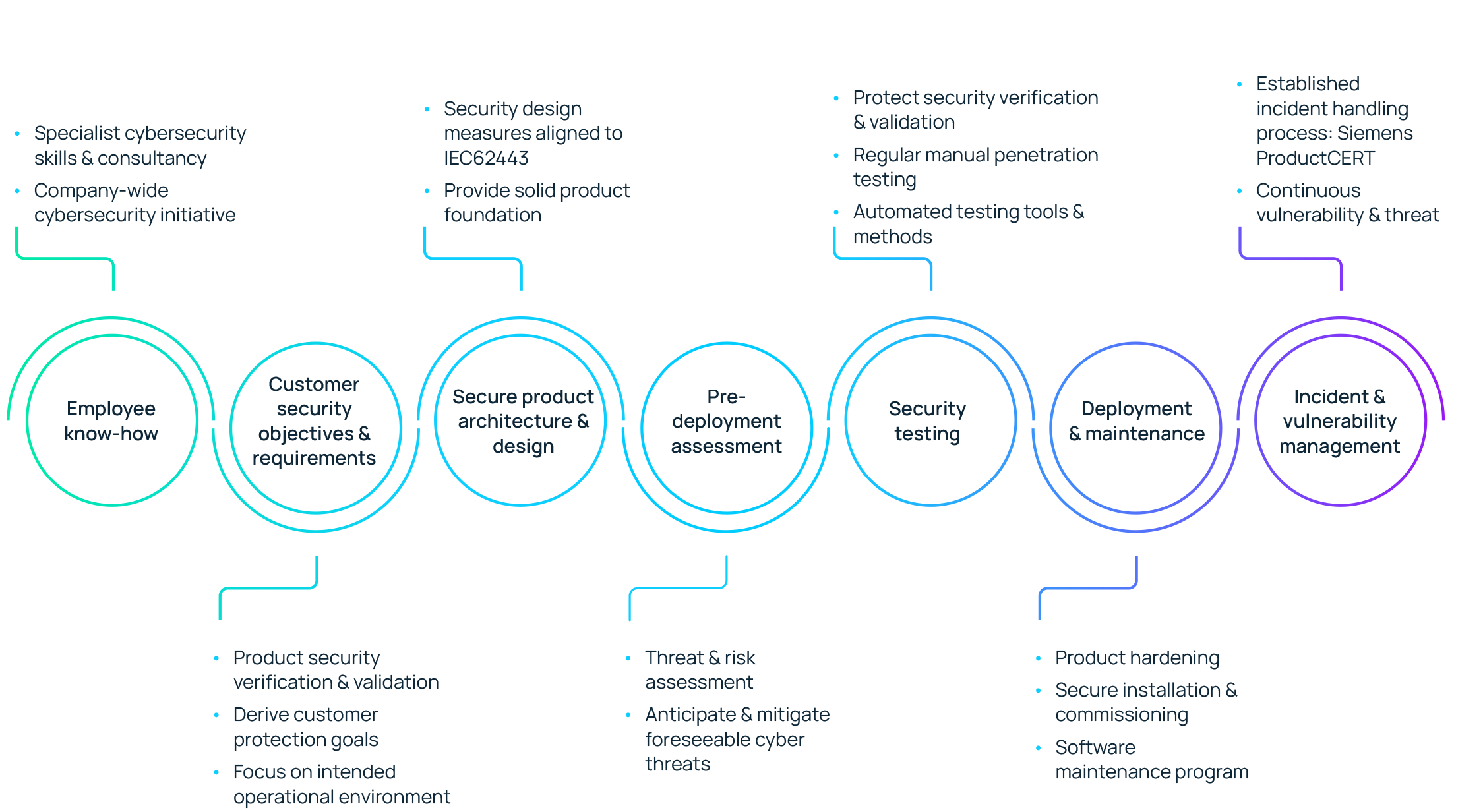
The effectiveness of a product’s cybersecurity design is attributed to the expertise of the development team. As part of our Security by Design methodology, we invest in technology developments for digital protection and product security and training required to maintain high levels of employee cybersecurity expertise.
Throughout the lifecycle of the product, our experts perform security threat and risk assessments (called TRAs) to address expected risks in the intended application of use. This assessment starts at the beginning of the process and is repeated as required to identify and mitigate risks appropriately.
In addition, Siemens AG and external experts conduct regular product security testing and use both manual penetration tests and automated machine security testing. The idea is to break the system in order to secure it. This testing ensures that the FIN Framework meets our security requirements. The test results are recorded and used to identify any necessary corrective actions.
Applying Security by Design
to FIN Framework
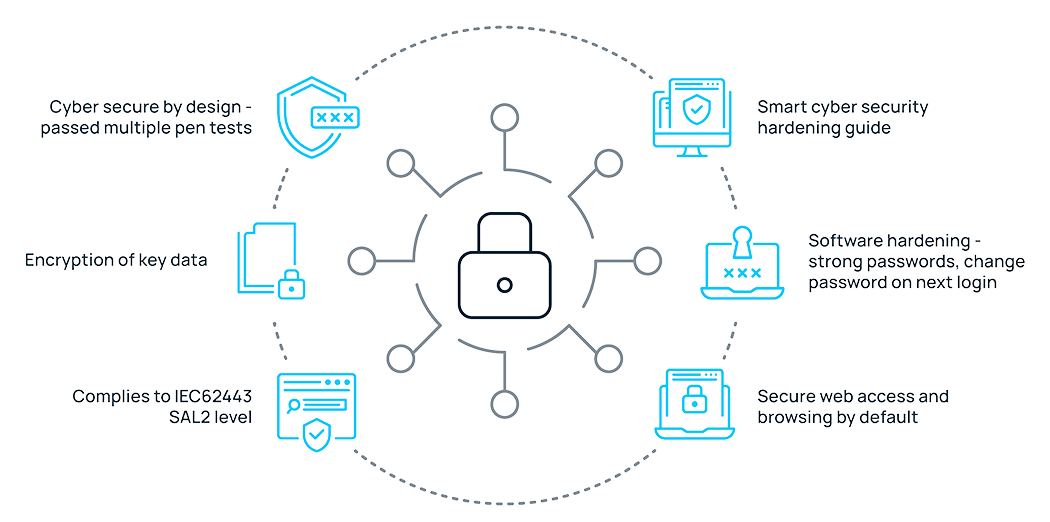
FIN Framework is an open and robust platform for building automation and IoT that is at the center of creating efficient, sustainable and comfortable environments. FIN Framework products are aligned with ISO/ IEC62443.
- End-to-end encryption from client to server
- End-to-end encryption between servers
- Encrypted communication to other devices
- Asymmetric Key Certificate-Based Encryption
- SLDAP Authentication
- Using the least privilege principle to limit data and application access
- Support of hardware and software firewalls
- SCRAM-SHA-256 authentication
- Sensitive Information is stored in an encrypted database

- Role-based authorization
- Action-based auditing
- Configurable password complexity enforcement
- Use of verified third-party components
FIN Framework Software Maintenance for highest level of Cybersecurity
As part of our Software Maintenance Program, we periodically release patches, updates, and platform upgrades that remove new known vulnerabilities and protect FIN Framework against threats.
Patches and updates are made available as they are developed, supported by access to a technical hotline run by product experts. By participating in the FIN Software Maintenance Program, you not only gain access to the latest innovation and new functionality, but also to the latest improvements in product robustness and cybersecurity.
FIN Framework Cybersecurity Deployment
We publish cybersecurity hardening guidelines to support the secure commissioning and deployment of FIN Framework products. These guidelines describe how the system needs to be configured in order to ensure secure operation of the FIN Framework product in the intended operating environment. The hardening guidelines are maintained throughout the product lifecycle.
Emergency Management
If a security issue or vulnerability is detected in a FIN Framework product or solution, we have incident and vulnerability handling processes in place.
FIN Framework software components are registered so that if any security vulnerabilities are found, the necessary remedies can be implemented and disclosed. Identified vulnerabilities are announced by the ProductCERT team via the ProductCERT security advisories.
Case studies
Discover how our customers have utilized FIN Framework in different use cases