The home of smart buildings, smart equipment and IoT

Connectivity and digitalization have created numerous advantages in the Building Automation industry. Flexibility, energy efficiency, increased building control, user comfort and more. But all of this connectivity brings new security challenges. Cyber attacks are on the rise and can be detrimental to a building. How do you confidently address such cyber threats? You have to take a holistic approach to cybersecurity. Not just within your IT department but across all aspects of your organization. That includes making sure the building automation systems that manage your facility’s infrastructure are secure.
Cybersecurity is defined as the protection of life and company assets from harm caused by digital attacks against the availability, confidentiality, integrity, authenticity, and reliability of information in cyberspace. At J2 Innovations, we take that very seriously and have adopted a “think security” philosophy in the development and advancement of our FIN Framework product.
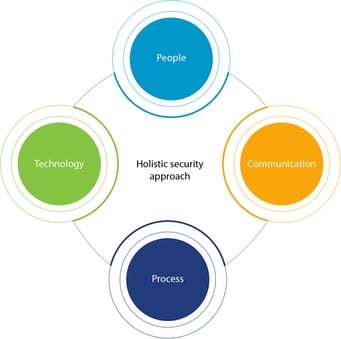
A holistic approach to cybersecurity means taking the following four key factors into account.
These key factors, if not taken into account, can be the downfall of security. People need a broad and lasting awareness of the importance of security (both physical and cyber). Clear and concise communication is important in establishing a culture of security. Processes are important for ensuring protection from cyber threats. Technology needs to be tested, vetted, and matched with other suitable building blocks in order to secure an organization’s assets.
You can have the most advanced and well-tested technology, but if your processes break down, or communications fail, cybersecurity can be threatened. You can have well-thought-out and thorough processes, but if people aren’t trained and a culture of security hasn’t been curated, your system can be left open to cyber-attacks through human error.
Are the developers of your building automation and IoT products experts in cybersecurity? Do they follow cybersecurity standards? At J2 Innovations, our developers are highly trained and follow strict standards to ensure that coding leads to secure product architecture, as well as secure implementation of software components.
The building technology products you choose should be “Secure by Design”, meaning security was built-in from the beginning rather than implemented as an after-thought. Quality assurance processes and cybersecurity best practices need to be used to ensure the software is not only the highest quality but also rigorously tested for security. At J2 Innovations, we are part of the Siemens group and jointly participate in the Charter of Trust, a global effort to develop and implement rules for ensuring cybersecurity throughout the networked environment. Regular product security testing is conducted by Siemens AG and external experts who use manual penetration tests alone or in combination with automated machine security testing. The idea is to break the system in order to secure it. This testing ensures the FIN Framework meets our security requirements.
Secure by Design also means that certain features and functions are secure at the default level to help prevent phishing incidents from happening. One example of that (what we call “secure by default”) can be seen in FIN’s new Host App. It includes security enhancements like strong password settings and better user management.
When choosing a product for building automation and IoT built on an open framework, it’s important to ensure the framework is being constantly tested and enhanced to ensure that the technology is never outdated and stays on top of the latest cybercriminal tactics.
The FIN Framework is highly extensible so that OEM partners can customize the product to meet their specific market and customer requirements. As an open platform and as the heart and brain of a building, security by design is an essential pillar for us.
Our FIN Framework design experts adhere to the Siemens company-wide cybersecurity initiative. They follow the mandatory internal security policy that provides measures for ongoing development of FIN Framework products in accordance with the appropriate security level. FIN Framework products are aligned with ISO/IEC62443.
A cyber-secure building technology product should also have a software maintenance program that frequently releases patches, updates, and platform upgrades to remove new known vulnerabilities discovered during ongoing testing.
At J2 Innovations, patches and updates are made available as they are developed, supported by access to technical hotline support run by product experts.
Your building technology product could be cyber secure, but its deployment could cause security issues. This is why it’s important that your technology partner has cybersecurity hardening guidelines to support the secure commissioning and deployment of FIN Framework products. These guidelines describe how the system needs to be configured in order to ensure secure operation of the product in the intended operating environment. Configuration options consist of, for example, which applications to install, which settings to activate or deactivate, firewall configurations, and the setting of user and system accounts and access rights.
We offer this for the FIN Framework. The hardening guidelines are maintained throughout the product life cycle.
Finally, your building automation and IoT platform needs to offer emergency management services in the event that something does happen. Incident and vulnerability handling processes need to be in place if there’s a security issue or a vulnerability is detected. The FIN Framework has a technical support team, which is supported by the global Siemens ProductCERT team. The necessary steps are taken to handle the situation and the incidents and remedies are disclosed.
Here’s a look at some of the features that make the FIN Framework “Secure by Design.”
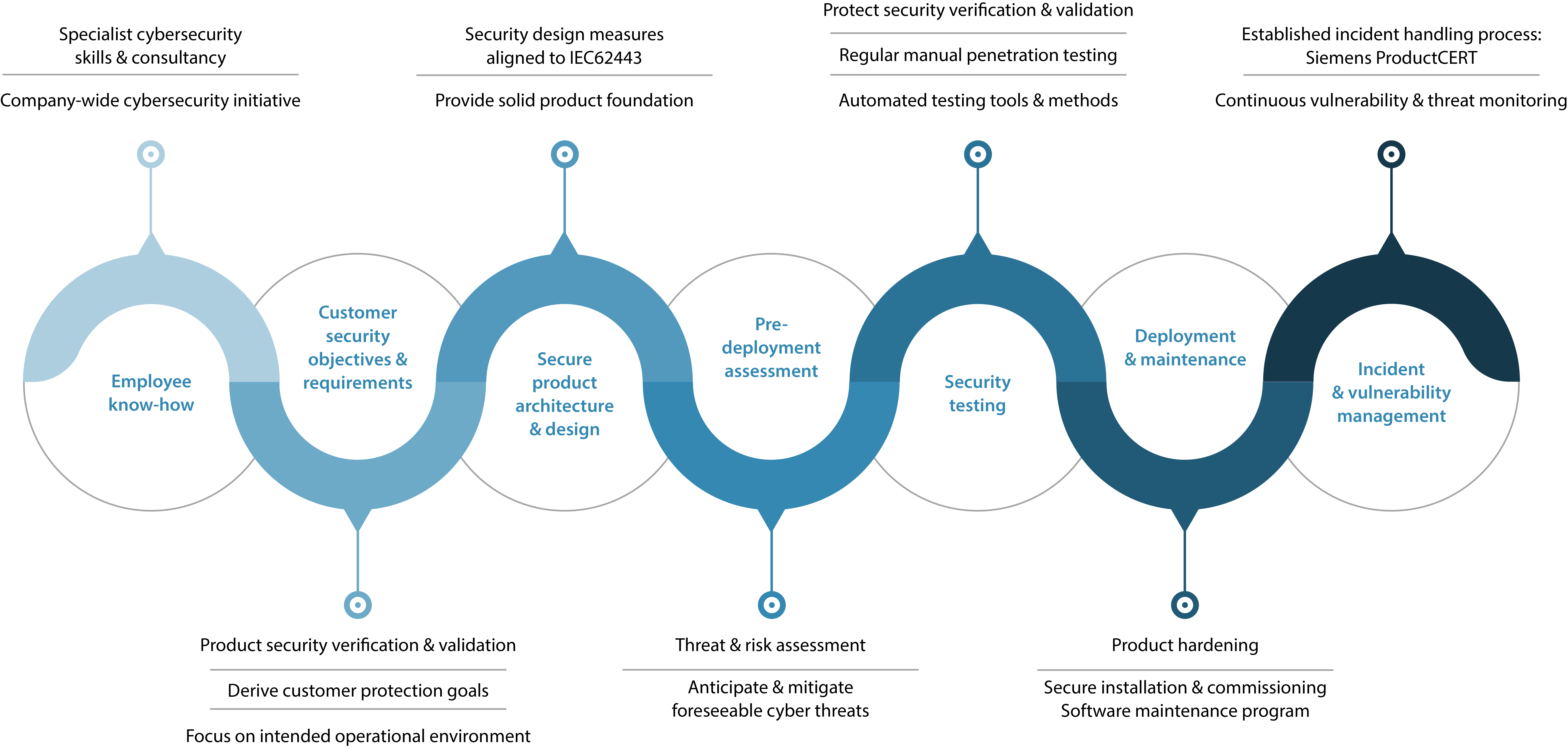
Our comprehensive security approach to the product life-cycle means our FIN Framework is designed with your security in mind. This ensures that FIN Framework can be part of your holistic approach to security that takes people, processes, technology, and communication into account.
Scott joined J2 Innovations as a partner in 2011 and is now Vice President of Knowledge Excellence. He has a wide range of responsibilities, including evangelism, business development and training. Scott is well known as an industry expert in smart homes and smart buildings. He is a past president of ASHRAE, and is currently a board member for Project Haystack. Scott attended Clarkson University for Mechanical Engineering and graduated with a BS/Business in Organizational Innovation.
Topics from this blog: FIN 5.0 Siemens Cybersecurity IoT Smart Buildings
Back to all posts
J2 Innovations Headquarters, 535 Anton Blvd, Suite 1200, Costa Mesa, CA 92626, USA. Tel: 909-217-7040