The home of smart buildings, smart equipment and IoT

Cyber attacks are a constant and increasing threat due to the ubiquitous connectivity that makes digitalization possible. In today’s connected world, the likelihood of a cyber attack is high, which is why maintaining cyber security is an important part of managing and operating a smart building.
We asked our VP of Engineering, Hisham Ennarah to share some simple, top level security tips in honor of Cybersecurity Awareness Month. Here’s what he shared.
Avoid opening ports for remote desktop services, which allow all sorts of attacks, instead set up a VPN for remote access.
Setup a firewall for your building automation network with whitelisting rules to protect your network from aunauthorized access.
Wireless LANs must be protected using state-of-the-art methodology. Otherwise, an attacker can join the wireless LAN bypassing the firewall protection.
Establish a strong password policy for BMS users' authentication. The policy configuration should identify the required frequency for changing the password. This is very important because it protects against a range of attacks. Automated password guessing bots have become very sophisticated.
Finally, be sure your BMS is “secure by design” meaning that it meets international security standards and cybersecurity guidelines. It also means that your software provider offers continuous testing, enhancements, and evolution of the product to ensure it remains cyber secure.
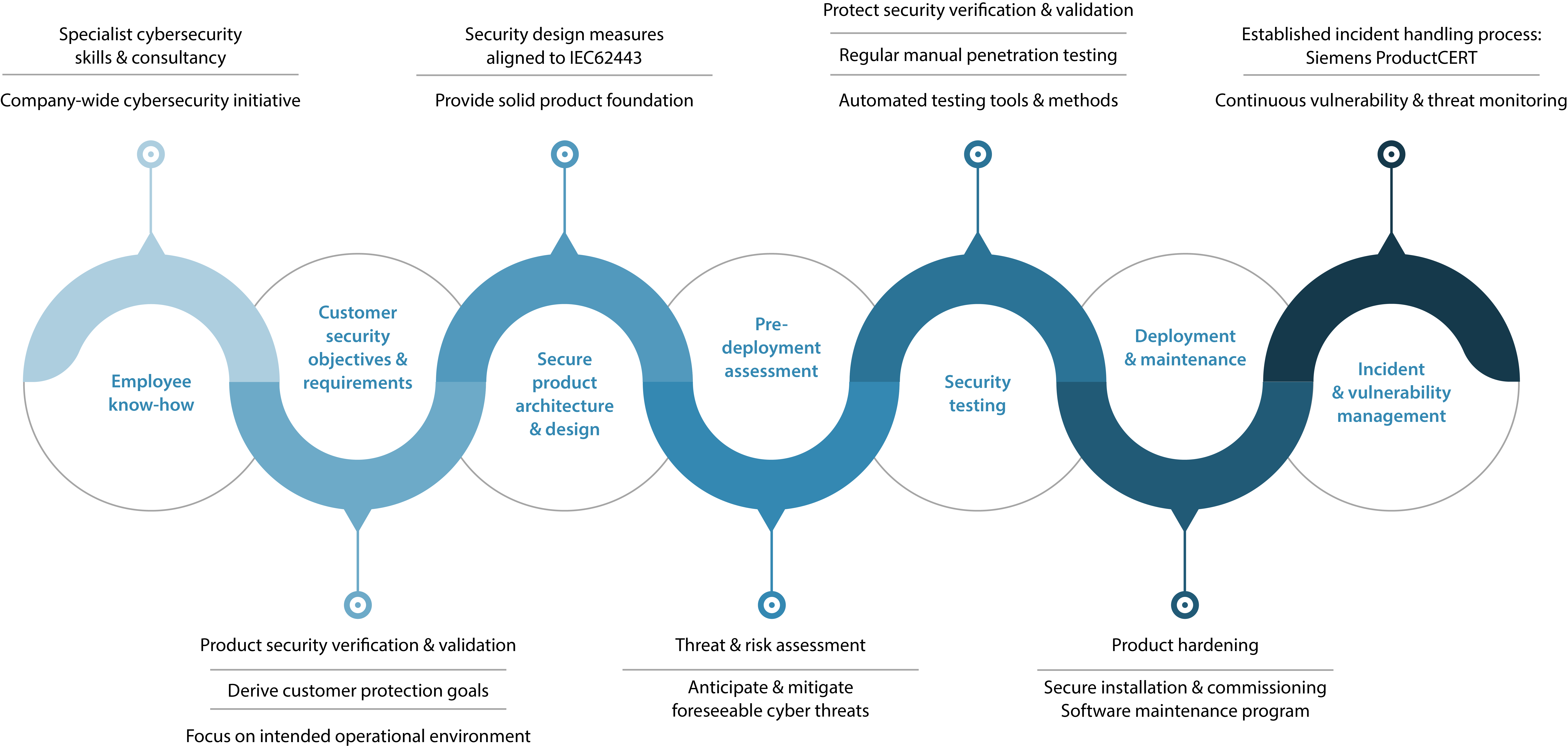
As part of J2’s "Security by Design" methodology, we invest not only in technology developments for digital protection and product security but also in the training required to maintain high levels of employee cyber security expertise. Throughout the lifecycle of the product, our experts perform security threat and risk assessments. In addition, product security testing is conducted regularly by Siemens AG and external experts who use both manual penetration tests and automated machine security testing.
Here’s a look at how that cycle works.
To learn more about Security by Design in the smart building industry, download our Cybersecurity whitepaper.
Scott joined J2 Innovations as a partner in 2011 and is now Vice President of Knowledge Excellence. He has a wide range of responsibilities, including evangelism, business development and training. Scott is well known as an industry expert in smart homes and smart buildings. He is a past president of ASHRAE, and is currently a board member for Project Haystack. Scott attended Clarkson University for Mechanical Engineering and graduated with a BS/Business in Organizational Innovation.
Topics from this blog: Cybersecurity Industry
Back to all posts
J2 Innovations Headquarters, 535 Anton Blvd, Suite 1200, Costa Mesa, CA 92626, USA. Tel: 909-217-7040